In the realm of Linux, one encounters a cryptic code that appears more like an alien language than anything comprehensible: lrwxrwxrwx. This code, however enigmatic it may seem, holds the keys to the kingdom of Linux file permissions. In this comprehensive guide, we will demystify the secrets of lrwxrwxrwx, breaking it down piece by piece, so you can gain a firm grasp of Linux file permissions and wield this knowledge with confidence.
The Basics of Linux File Permissions
Understanding File Permissions
File Permissions (rwx)
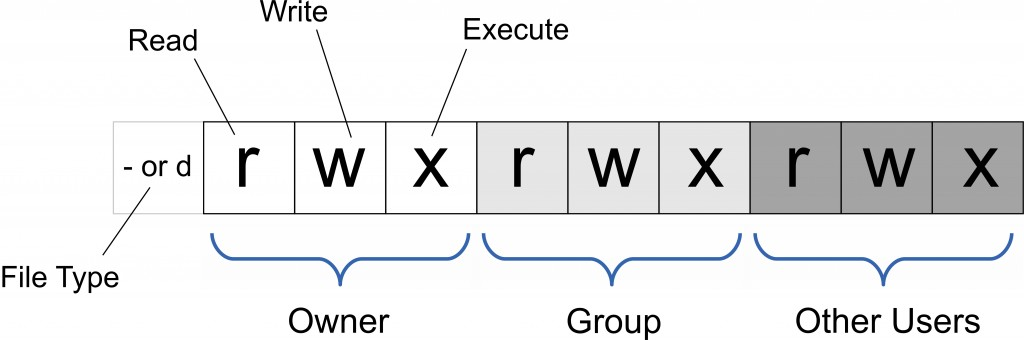
Linux employs a robust system of file permissions represented by the lrwxrwxrwx code. Each of these characters signifies a specific aspect of file control:
- l: Denotes the file type. In this case, it’s a symbolic link;
- r: Indicates read permission;
- w: Signifies write permission;
- x: Represents execute permission.
Decoding the lrwxrwxrwx Code
Now that we’ve cracked the code, let’s put it into action:
- lrwxrwxrwx: The first ‘l’ tells us this is a symbolic link.
- The following rwx triads refer to permissions for the owner, the group, and others, respectively;
- Owner (rwx): The owner of the file has read, write, and execute permissions;
- Group (rwx): Members of the file’s group share the same permissions;
- Others (rwx): Anyone else gets identical permissions.
Advanced Concepts in Linux Permissions
Special Permissions
Linux file permissions aren’t just limited to lrwxrwxrwx. There are special permissions to consider:
- SUID (Set User ID): When set, the file runs with the owner’s privileges;
- SGID (Set Group ID): Similar to SUID, but runs with group privileges;
- Sticky Bit: Ensures only the owner can delete or modify a file in a shared directory.
Numeric Representation
While lrwxrwxrwx provides a human-readable overview, numeric representation condenses permissions for easy scripting. For instance, rwxr-xr-x can be represented as 755, where each digit corresponds to a permission level.
Changing Permissions
You can modify permissions using the chmod command, followed by the permission code and the filename.
Practical Applications
Examples of Linux File Permissions
Let’s explore some real-world scenarios:
Example 1: Securing Sensitive Files
Suppose you want to protect a file called secret.txt. You can restrict access to just the owner while denying group and others any access

Example 2: Shared Development Folder
In a collaborative environment, you might want to allow group members to read and write files within a shared folder but prevent deletion:

Linux vs. Other Operating Systems
Contrasting File Permissions
Linux’s approach to file permissions differs significantly from other operating systems like Windows. Windows relies on access control lists (ACLs) for granular control, whereas Linux uses a more straightforward but robust permission system.
Best Practices for Linux File Permissions
Securing Your System
To ensure your Linux system remains secure:
- Regularly review and audit file permissions;
- Limit access to sensitive files;
- Avoid using overly permissive settings;
- Utilize special permissions judiciously;
- Implement user groups effectively.
Conclusion
Congratulations! You’ve successfully decoded the enigmatic lrwxrwxrwx and delved into the intricate world of Linux file permissions. Armed with this knowledge, you can confidently navigate the Linux file system, safeguard your data, and ensure the security of your Linux-based systems.
FAQs
The ‘l’ indicates that the file in question is a symbolic link.
You can change file permissions in Linux using the ‘chmod’ command, followed by the desired permission code and the filename.
Numeric representation condenses permissions, with each digit corresponding to a permission level. For example, ‘rwxr-xr-x’ can be represented as ‘755’.
Properly managing file permissions is crucial for system security, data protection, and controlling access to files and directories.
While Linux primarily uses traditional file permissions, ACLs can also be employed for finer-grained access control if needed.